In our last blog series we discussed multiple access commands that can be configured on a router or a switch. These commands included cosmetic commands such as logging synchronous and exec-timeout that can be configured on the console port. We also discussed configuring security features such as banners that can be used for legal purposes.
For this discussion we will compare Telnet and Secure Shell protocol (SSH). Both protocols can be used for remote access but their differences are important to any network technician or engineer.
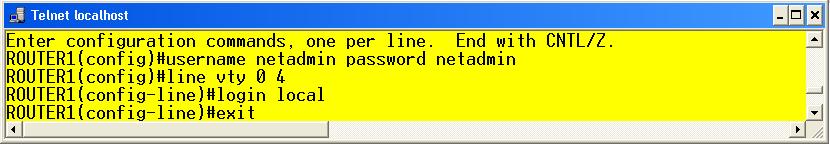
First, to gain remote access to the Virtual Terminal Teletype lines (VTY), a router or switch must be reachable with a given routed protocol. This would include IPv4 or IPV6. (This seems obvious but it will be quite useful later in a future discussion.) Additionally, for the access lines you must configure either a line password, or local user database for the way to authenticate to the device. In example 1 you will see our basic access to setup the default telnet lines to this router.
As you can see, a basic password has been configured. The other option (shown in example 2) is to use the local user database.
In either case, if someone need to gain access to this device they will have to login with the authentication type that was specified.
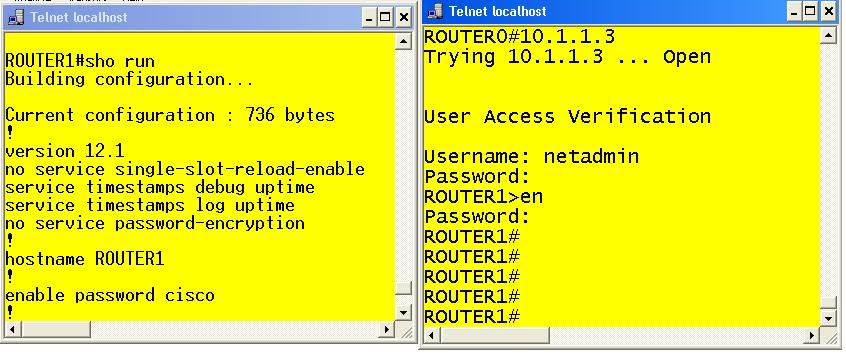
Second, by default Telnet is associated with the VTY lines. Telnet uses TCP port number 23 and is one of the most commonly used protocols for remote access. However, telnet doesn’t have any type of confidentiality. In other words, it has no encryption mechanism. Eavesdroppers can easily discover messages that are passed between two devices using telnet, in fact programs such as Wireshark or Ethereal can see the passwords inside the telnet packets. In example 3 you can see that the router on the right (ROUTER 0) is telneting to the router on the left (ROUTER 1). Notice that I created an enable password of cisco on ROUTER1.
EXAMPLE 3
Example 4 displays the vulnerability of telnet. As shown, I have a Wireshark looking at the messages that are going between these two routers. The frame that was captured shows inside the telnet data, the password cisco being sent in one of the messages.
(Ok, it says "cisc", but frame 66 contains the letter "o" so with work, a skilled hacker or even a novice can see these messages sent in clear text.)
The other common application for remote access to Cisco routers and switches is Secure Shell protocol (SSH). SSH runs on TCP protocol number 22 and unlike telnet, does include encryption. SSH also uses a more commands for setup in comparison to telnet. The first necessary command is to configure a local user database as illustrated in example 2. The next command is mandatory, SSH needs to have a key for its connection. This key is derived from the ip domain-name command. Example 5 displays creating a unique (local) domain-name for the router.
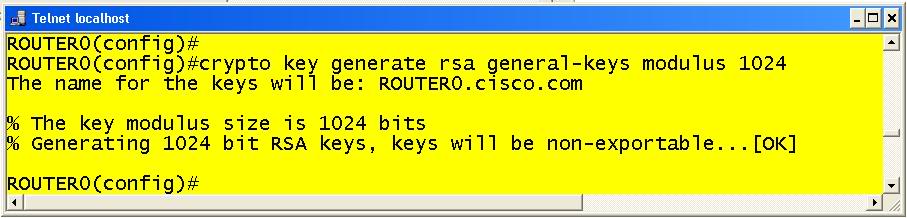
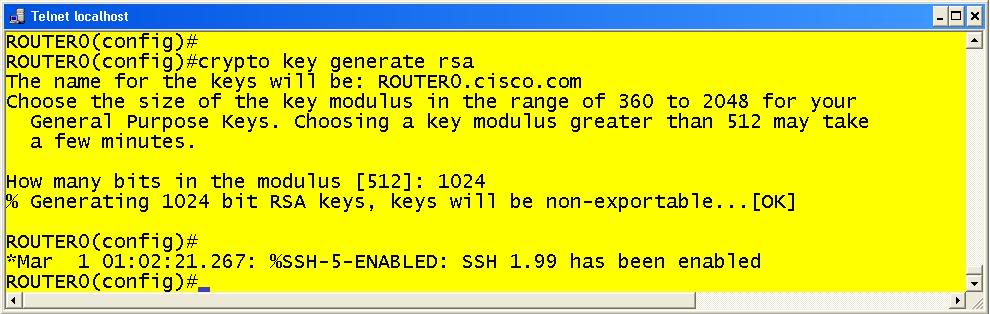
After this is done you must generate a key. This is done with the command crypto key generate rsa. Examples 6 and 7 display two different ways to use the command it’s configuration for the rsa keys.
Example 6 is the full blown way of configuring the general key. Example 7 displays the more interactive version of this command. This is useful for those that don’t know which key size may be necessary for a given application. Also, demonstrated in example 8 is the crypto key zeroize command which will erase the key.
Next, you must enable an SSH version and apply it to the VTY Lines. First with the global configuration commands ip ssh version <1 or 2>, you can specify which version of ssh will be used for access. Second, you must configure the vty lines for authentication to the local database with the line command login local and specify that only ssh will be permited to access these lines with the command transport input ssh (transport input ssh telnet means only these two protocols will have access to the VTY lines. The default is transport input all for all types of protocols.) These commands are displayed in the next example.
EXAMPLE 9
The most common ssh client program used is called putty. It is a freeware application that is used for telnet, ssh and other programs. Example 10 demonstrates basic configuration and successful access of ssh via putty.
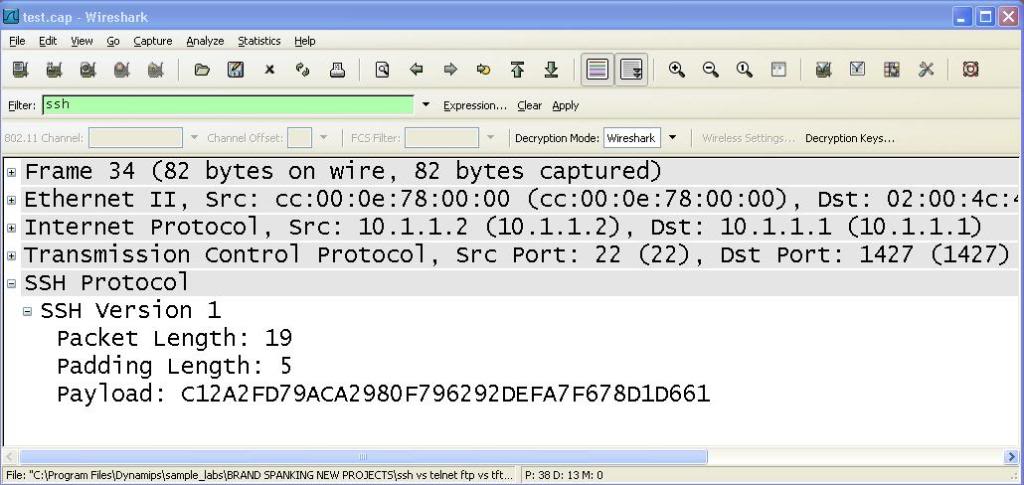
Example 11 below, is a contrast to example 4. You can see that the passwords aren’t shown and that the datagrams are encrypted above the layer 4 header. This gives SSH the advantage compared to telnet in all remote access scenarios.
This now concludes our comparison of Telnet vs SSH. You can clearly see the advantages of SSH and why it becoming a well recognized security standard and accepted practice in the computer networking industry.


 Worldwide Locations
Worldwide Locations